What Is DMARC? Email Security & Authentication
Spammers are constantly looking for hacking opportunities in your email, from spoofing your email domain to sending phishing messages to your inbox. If you don't comply with the best email practices to improve the deliverability of your emails, it could make you a victim. Luckily, it's easy to protect your domain from email spoofing with Domain-based Message Authentication, Reporting, and Conformance (DMARC). In this article, learn what DMARC is and how the records work to protect your email domain against threats.
What is DMARC?
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It's an email authentication protocol designed to help prevent spammers from forging your domain in a process also known as domain spoofing.
Attackers can forge the From address on an email message so that it appears to come from a user in your domain. This common tactic used in email-based attacks tricks recipients into taking actions that may compromise privacy.
Domain-based Message Authentication, Reporting, and Conformance allows email domain owners to specify their own authentication procedure, which covers how their email should be authenticated and what actions should be taken if the authentication fails. Once the DMARC DNS entry is published, fraudulent emails get blocked before they reach your inbox. Therefore, the main purpose of deploying the protocol is to protect a domain from being used in cyber threats.
What is DMARC record?
A DMARC record is a DNS TXT record that tells receiving mail servers what to do with emails that fail authentication. These records operate at the domain level and are therefore published in the domain name system (DNS).
This record stores a domain's DMARC policy. It includes important parameters such as the p tag, which specifies the policy to apply, and the rua and ruf tags, which specify the email addresses where DMARC reports should go. Proper DMARC record configuration effectively protects your domain from email spoofing.
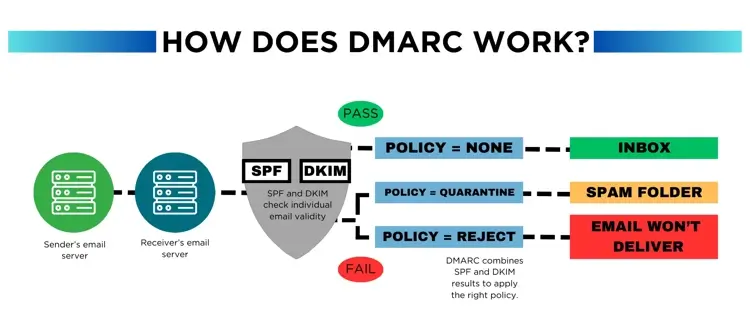
How does DMARC work?
Domain-based Message Authentication, Reporting, and Conformance works with DKIM (DomainKeys Identified Mail) and SPF to authenticate the sender of an email. The protocol requires either of the two, or both, to be in place on an email domain. SPF checks the IP address of the sender to make sure it has authorization to send emails on behalf of your domain. DKIM, on the other hand, adds a digital signature to every sent message to verify the integrity of its content.
The protocol then adds an additional layer of protection by allowing domain owners to specify how email receivers should handle emails that fail SPF or DKIM checks.
First, the recipient's mail server checks for a DMARC record for the sending domain by performing a DNS lookup for the record. The DMARC record is a TXT record published in the DNS zone of the sending domain. Then, if there is a record, the mail server checks to see if the email passes SPF and DKIM authentication. To do this, it compares the IP address of the sender to the list of authorized IPs and verifies the digital signature on an email.
If the email passes SPF or DKIM authentication, then the mail server delivers it to the inbox. However, if it fails SPF or DKIM authentication, the mail server takes action based on the instructions in the DMARC record. The record can specify one of three actions that the mail server should take if the email fails SPF or DKIM authentication.
Three actions taken in authentication failure
Domain-based Message Authentication, Reporting, and Conformance records choose one of the following actions to take should an email fail SPF or DKIM authentication.
- No action. In some cases, the server delivers the email to the recipient's inbox even if it fails SPF or DKIM checks.
- Quarantine. The mail server moves the email to a spam folder instead of an the inbox, where the recipient can view it later.
- Reject. The server can block the message and reject the email, making it so that the recipient doesn't get it.
Note that not all mail servers support DMARC. However, support for the protocol is growing, and many of the largest mail servers use it today.
What does DMARC look like?
The structure of a DMARC record is defined in RFC 7489, which was published in March 2015. The standard defines the DMARC record format as well as the various tags and values that work in the protocol records. Consider the following example of a Domain-based Message Authentication, Reporting, and Conformance record.
_dmarc.example.com IN TXT "v=DMARC1; p=reject; rua=mailto:[email protected]; ruf=mailto:[email protected]; sp=reject"
These sections within the record signify different instructions and information.
- _dmarc.example.com refers to a special subdomain that is used for records. In this case, it's "example.com."
- IN TXT means that the record is a TXT record.
- v=DMARC1 specifies the version of DMARC being used. DMARC1 is the current version in use.
- p=reject indicates the policy for emails that fail SPF or DKIM authentication. The reject policy also tells receiving email servers to reject emails that fail authentication.
- rua=mailto:dmarc@examplecom signifies the email address to send DMARC aggregate reports to. These aggregate reports provide information about how many emails passed and failed authentication, as well as the reasons for failures.
- ruf= mailto:[email protected] specifies the email address to send DMARC forensic reports to. Forensic reports provide more detailed information about emails that failed authentication.
- sp=reject sets receiving email servers to reject emails from subdomains that fail authentication.
Why use DMARC?
There are many benefits to using the Domain-based Message Authentication, Reporting, and Conformance protocol. From improved email security to easy access to authentication reports, consider the following reasons to use DMARC.
Enhanced email deliverability
DMARC plays a crucial role in improving email deliverability because organizations that implement it are able to authenticate their emails and ensure that email providers don't mark them as spam. This leads to higher chances of emails reaching the recipients' inbox, increasing the effectiveness of communication.
Increased email security
In conjunction with DKIM and SPF, DMARC allows email receivers to verify the authenticity of incoming emails. It checks the alignment between the domain in the email's header and the domain used to send the email.
If the alignment fails, the email receives a rejected mark, preventing malicious actors from impersonating legitimate senders. Protection against email spoofing helps maintain the integrity of email communications.
Visibility into email authentication
The protocol lets you receive detailed reports on the authentication status of your emails. These reports provide valuable insights into which emails are failing, passing, or being spoofed. It therefore becomes easier for domain owners to not only identify but also take action against unauthorized senders.
Additionally, Domain-based Message Authentication, Reporting, and Conformance reports can help domain owners identify any issues with their email authentication setup.
Improved brand reputation
Domain-based Message Authentication, Reporting, and Conformance protects your brand reputation by preventing others from impersonating your domain. It stops cyber attackers from spreading spam, malware, and phishing emails using your brand.
What is a DMARC policy?
A DMARC policy informs the receiving email servers what to do after checking an email against DKIM and SPF. An email message passes or fails either of these authentication tests.
You have to create a Domain-based Message Authentication, Reporting, and Conformance policy for each domain you wish to protect. These policies instruct receiving email servers to either None, Quarantine, or Reject messages that fail authentication checks. A good example of a policy is:
v=DMARC1; p=quarantine; rua=mailto:[email protected]
This policy tells receiving mail servers to quarantine emails that fail DMARC authentication. It also requests that aggregate DMARC reports go to the email address [email protected]. These policies record as machine-readable commands rather than as human-readable sentences so that email services can understand them.
What is a DMARC report?
DMARC reports contain essential information about the authenticity status of emails sent on behalf of a domain. A DMARC report tells you:
- What percentage of email messages passed or failed DMARC evaluation
- What are the sources of the emails
- What actions the receiving email server takes on unauthenticated messages from your domain
- Which servers send emails that fail the protocol
- Which policies are applied to emails
It's advisable to always use reports when you enable DMARC for your domain. This helps monitor the effectiveness of your email authentication process.
Reports are available in two formats: aggregate reports and failure reports. Aggregate reports provide a high-level overview of authentication status of DMARC, DKIM, and SPF. They can be used to identify problems with your email. They include data on the volume of emails sent from the domain, the email servers used, and more.
Failure reports, on the other hand, provide detailed information about individual email messages that failed DMARC checks. They can include the email's content, header information, and details about the failed authentication mechanisms.
How to set up DMARC
Setting up DMARC for your domain requires a few steps. They are as follows:
- Identify valid sources of mail for your domain. This includes all of the email servers and services that send mail on behalf of your domain, such as your email marketing provider, CRM system, and website contact form.
- Set up SPF for your domain. SPF is an email authentication protocol that allows you to specify which IP addresses receive authorization to send mail on behalf of your domain.
- Set up DKIM for your custom domain. DKIM is another email authentication protocol that allows you to sign your outgoing emails with a digital signature. This helps to ensure that your emails remain unaltered in transit.
- Form the DMARC TXT record for your domain. The DMARC TXT record is a DNS record that tells receiving mail servers what to do with emails that fail SPF or DKIM authentication.
Once you've set it up, use a DMARC lookup tool to check for any issues in the established system.
Frequently asked questions
How does DMARC protect against phishing?
Domain-based Message Authentication, Reporting, and Conformance makes it difficult for attackers to impersonate your domain in an email. if you have a DMARC policy out of quarantine or reject, phishing emails that pretend to be from your domain will either go in the spam folder or receive rejection.
Can I use DMARC without SPF or DKIM?
No, DMARC is designed to be used with SPF and DKIM. To use DMARC, you must have at least one of these two mechanisms in 0place. However, the best practice is to have both set up for maximum protection.
What is the relationship between DMARC, DKIM, and SPF?
DMARC ties the two protocols together with a consistent set of policies. It allows the email receiver to check that an email aligns with what the sender's SPF and DKIM records say about it.
What is alignment in DMARC?
DMARC alignment means that the domain in the From address of the email matches the domain used in the SPF or DKIM check.
What if my DMARC isn't working?
If your record isn't working, use a DMARC checker tool to test DMARC validation and accuracy. With a check tool, you'll be able to see if your record has an error message, needs updates, and more.