What Is Cryptography? Understanding Methods and Applications
Cryptography may seem like an obscure, complex topic at first glance. However, in truth, cryptography and encryption methods are used frequently, even in day-to-day life. In this article, learn what cryptography is and the various kinds of encryption used to keep data safe, including asymmetric encryption, symmetric encryption, and hash functions.
What is cryptography?
In computer technology, cryptography is a term for the technique of turning messages or data into a private, unreadable form referred to as ciphertext. Essentially, cryptography privatizes messages to secure the data inside, making it so that only the intended recipients can get access. Because it protects messages so well, cryptography is beneficial for senders to need to deliver messages across open or public networks. It also helps to ensure that third parties don't alter the message or data sent across the network during transportation.
Users can utilize several different cryptography techniques to protect the contents of messages. However, the most common are pairs of symmetric or asymmetric keys.
Methods of cryptography
Cryptography relies on several different methods to protect sensitive information. The most common methods are via symmetric encryption, asymmetric encryption, and hash functions.
Symmetric key cryptography
Symmetric and asymmetric encryption both use keys to secure and unlock information. These keys aren’t physical; rather, they are digital bits or characters.
Imagine you wanted to deliver important, private papers to a friend, so you locked them in a box. You’d have one of the keys needed to open the lock. But then, to your friend, you’d give the other key. Only the two of you would have the right keys to open the box, keeping the information secure.
Symmetric and asymmetric keys work the same way for cryptography.
While both symmetric and asymmetric encryption function similarly, they differ in terms of keys. Symmetric key encryption only uses one key on both ends. It encrypts and decrypts with the same key.
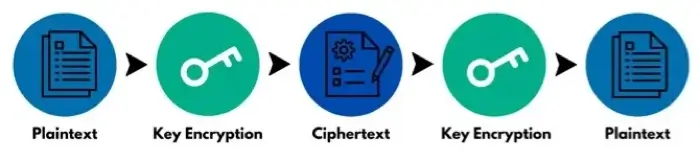
Therefore, it's crucial that the key be kept secure. Key interception makes it challenging for either party to encrypt or decrypt the data or message.
Common examples of symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
AES blocks use a fixed length of 128 bits, but it can use keys of various sizes, from 128 bits to 256 bits. It is best at encrypting large amounts of data, making efficient and secure. AES became the standard encryption algorithm for many, especially given that it works with numerous different encryption modes.
Though AES replaced DES as the encryption standard, many still use DES, making it a popular symmetric encryption method. It uses a smaller key - 56 bits - and a smaller block size of only 64 bits. The small key size makes DES more susceptible to hacking incidents, but for smaller or low-security applications, DES still works well to encrypt messages and secure communications.
Asymmetric key cryptography
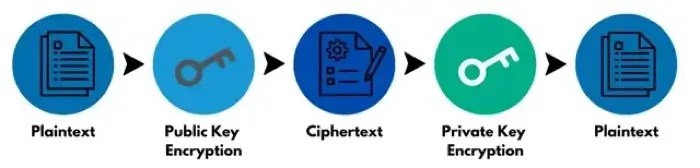
Unlike symmetric encryption, asymmetric encryption uses both public and private keys for each task. It uses a public key, which encrypts data, and a private key, which then decrypts that same data. The two keys are related, but they can't be derived from each other, making both keys individually secure.
Once data is encrypted with a public key, it's sent to the recipient. Public key cryptography allows one keyholder to encrypt many messages or data files with the same key. However, since only the recipient has the private key necessary to decrypt the data, it ensures that the data sent hasn't been tampered with or changed. Asymmetric encryption is often considered more secure than symmetric encryption for this reason.
Digital signatures are one popular example of asymmetric encryption. They ensure that the message remained in its original state during its course of transport. It’s like a piece of tape or a wax seal on a letter; when the recipient gets it, they know that nobody else has opened or viewed the message, so it’s secure.
Digital signatures work through asymmetric encryption keys; the sender marks the data or message with their private key and then sends it on its way. With the public key, then, the recipient can make sure that the signature is authentic and indeed generated by the sender. If the signature is legitimate, then the recipient knows the message arrived securely.
Other asymmetric encryption algorithms are RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography), and Diffie-Hellman Key Exchange.
Hash functions
Hash functions, or hashing, is a way for recipients to make sure that the data or message they receive hasn’t been changed or altered on its way. It essentially creates a digital summary of a message, which means each hash is unique.
Once the recipient gets the message, they too will create a hash of the message they received. If both hashes are the same, it indicates the message arrived unchanged and secure. However, if one of the hashes differs from the other, then it indicates that someone else made changes to the data somewhere along the way.
Examples of hashing algorithms include SHA-1 (Secure Hash Algorithm 1), SHA-2 (Secure Hash Algorithm 2), SHA-3 (Secure Hash Algorithm 3), BLAKE2, and MD5 (Message-Digest Algorithm 5).
Applications
Though it may seem like cryptography is an advanced IT solution with no use in day-to-day life, this couldn’t be farther from the truth. Cryptography protects all sorts of sensitive information – from credit card numbers to bank account data to passwords for accounts. Essentially, you can encrypt anything sent over a computer network for better protection.
It also helps prevent document tampering or interference with private documents for businesses or individuals. Any information that needs an additional level of security can benefit from cryptography.
VPNs (virtual private networks) also use cryptography to encrypt data between your computer and the network you connect to. The encryption tunnel prevents data from theft or damage as it travels across networks. Other security architectures, like Zero Trust Network Access (ZTNA), use cryptography elements as well.
If you operate a database or any data storage center, encrypting the data in that center can help protect you or your company from losses. Especially for centers dealing with sensitive, personal information – like medical records or personnel files – cryptography offers many much-needed benefits.
With methods such as digital signatures and hashing, cryptography also helps to authenticate identities, both of the sender and the recipient. When you need certain credentials to open or view information, it ensures that only the intended party can involve themselves with the message or data.
Frequently asked questions
What is the most well-known type of cryptography?
The most well-known type of cryptography is AES, or Advanced Encryption Standard. It’s a form of symmetric encryption that replaced DES (Data Encryption Standard) and has been the USA’s standard for encryption since 2001, meaning that all federal-level encryption must reach AES standards.
What are the three types of cryptography?
The three types of cryptography are symmetric encryption, asymmetric encryption, and hash functions.
Who invented cryptography?
Cryptography doesn’t have one specific inventor, as it has evolved over hundreds of years to become what it is today. It existed in various forms as early as the ancient Greeks. However, many consider Claude Shannon to be the father of modern mathematical cryptography starting in 1945.